 With dozens of millions of active users a day, uTorrent has long been the most used torrent client.
With dozens of millions of active users a day, uTorrent has long been the most used torrent client.
The software has been around for well over a decade and it’s still used to shift petabytes of data day after day. While there haven’t been many feature updates recently, parent company BitTorrent Inc. was alerted to a serious security vulnerability recently.
The security flaw in question was reported by Google vulnerability researcher Tavis Ormandy, who first reached out to BitTorrent in November last year. Google’s Project Zero allows developers a 90-day window to address security flaws but with this deadline creeping up, BitTorrent had remained quiet.
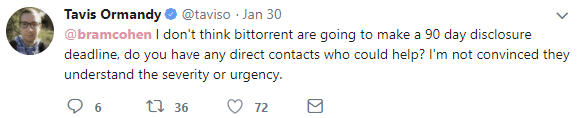
Late last month Ormandy again reached out to BitTorrent Inc’s Bram Cohen, fearing that the company might not fix the vulnerability in time.
“I don’t think bittorrent are going to make a 90 day disclosure deadline, do you have any direct contacts who could help? I’m not convinced they understand the severity or urgency,” Ormandy wrote on Twitter.
While Google’s security researcher might have expected a more swift response, the issue wasn’t ignored.
BitTorrent Inc has yet to fix the problem in the stable release, but a patch was deployed in the Beta version last week. BitTorrent’s Vice President of Engineering David Rees informed us that this will be promoted to the regular release this week, if all goes well.
While no specific details about the vulnerability have yet to be released (update below), it is likely to be a remote execution flaw. Ormandy previously exposed a similar vulnerability in Transmission, which he said was the “first of a few remote code execution flaws in various popular torrent clients.”
BitTorrent Inc. told us that they have shared their patch with Ormandy, who according to the company confirmed that this fixes the security issues (update below).

“We have also sent the build to Tavis and he has confirmed that it addresses all the security issues he reported,” Rees told us. “Since we have not promoted this build to stable, I will reserve reporting on the details of the security issue and its fix for now.”
BitTorrent Inc. plans to release more details about the issue when all clients are patched. Then it will also recommend users to upgrade their clients, so they are no longer at risk, and further information will also be available on Google’s Project Zero site.
Of course, people who are concerned about the issue can already upgrade to the latest uTorrent Beta release right away. Or, assuming that it’s related to the client’s remote control functionality, disable that for now.
Update: The vulnerability affects ‘recent’ unpatched uTorrent versions, not just those that have the Web UI enabled. (to clarify, older versions may not have the exploitable RPC server)
Update: More details about the vulnerability (and a demo) have been published by Ormandy after we finished this article. It is indeed a DNS rebinding issue that potentially allows outsiders to remotely execute code through uTorrent’s remote control feature.
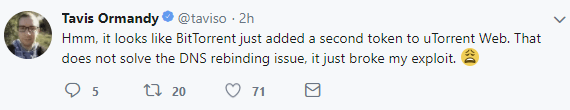
Also, uTorrent’s patch appears not to be as solid as BitTorrent Inc. believes, according to Google’s security researcher.
“Hmm, it looks like BitTorrent just added a second token to uTorrent Web. That does not solve the DNS rebinding issue, it just broke my exploit,” he writes.
and…

Update 2: BitTorrent inc just released the following statement:
“On December 4, 2017, we were made aware of several vulnerabilities in the uTorrent and BitTorrent Windows desktop clients. We began work immediately to address the issue. Our fix is complete and is available in the most recent beta release (build 3.5.3.44352 released on 16 Feb 2018). This week, we will begin to deliver it to our installed base of users. All users will be updated with the fix automatically over the following days. The nature of the exploit is such that an attacker could craft a URL that would cause actions to trigger in the client without the user’s consent (e.g. adding a torrent).
A fix for uTorrent Web was released a few hours ago according to BitTorrent Inc and users are recommended to update this to the latest available build as well.
To be continued.
—
Note: uTorrent’s Beta changelog states that the fixes were applied on January 15, but we believe that this should read February 15 instead.
Update: On February 22 BitTorrent Inc reports that patched versions are available now. More details and info are available here.





