![]() Grindr bills itself as the “largest social networking app for gay, bi, trans and queer people.” Back in March the company faced a crisis with reports of security breaches with privacy implications.
Grindr bills itself as the “largest social networking app for gay, bi, trans and queer people.” Back in March the company faced a crisis with reports of security breaches with privacy implications.
The first involved the use of a third-party website, which was able to extract normally hidden information from Grindr, including the email addresses and locations of people who had opted not to share that data.
The second alleged that unencrypted location data was being sent by the Grindr app, something the company later denied. A third report indicated that Grindr had been sharing users’ HIV status with outside companies.
Then, less than two weeks ago, a further report criticized Grindr for the existence of a third-party app known as ‘Fuckr’. Released back in 2015, Fuckr gives users the ability to precisely locate hundreds of Grindr users to an accuracy of just a few feet, a privacy nightmare for those not looking for that kind of immediate intimacy.
“The technique used to locate Grindr users is called ‘trilateration’. Hereby, the distance towards a certain user is measured from three (or more) virtual points nearby them,” Queer Europe reported.
“This can be done by making a call to Grindr’s server, which is accessible via an API (Application Programming Interface). After having obtained the distance between users and the three virtual locations nearby them, it is simple to find out where they are located.”
As revealed by Github, Grindr took almost immediate action. Via a DMCA notice, the dating service demanded that the entire ‘Fuckr’ repository be taken down from Github.
“The purpose of ‘Fuckr’ is to facilitate unauthorized access to the Grindr app by circumventing Grindr’s access controls, such that ‘Fuckr’ functions as ‘an unofficial desktop Grindr client’,” the notice reads.
“Among other things, the Grindr app contains mechanisms that prevent users from identifying the precise geographic locations of other users. ‘Fuckr’ is designed to bypass those mechanisms such that users can ‘[p]inpoint any guy’s exact location’.”
Grindr also points out that Fuckr is able to spoof a user’s location as well as granting access to otherwise non-downloadable images. For these reasons, Grindr states that Fuckr is primarily designed for the purpose of “circumventing a technological measure that effectively controls access to a work” protected under the Copyright Act. Github responded by deleting the repository.
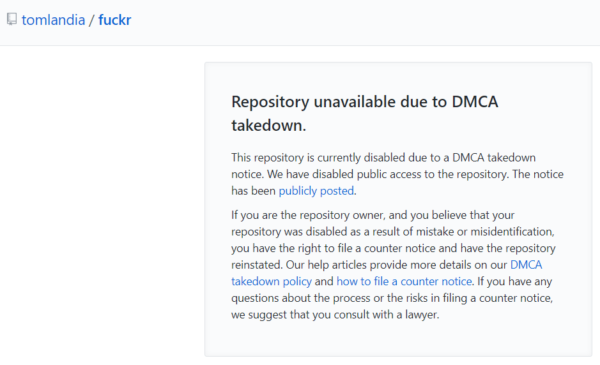
But while the immediate threat appeared to be over, Fuckr wasn’t dead just yet. Plenty of forks of Fuckr remained available and now it appears Grindr is engaged in a game of Whac-a-Mole to have them taken down. In a fresh DMCA notice filed with Github yesterday, the dating platform demanded that dozens of ‘forks’ of the software be taken down.
“As you are aware, we previously submitted a takedown notice for the ‘Fuckr’ repository ([repository disabled per previous DMCA takedown]) as it violated the Copyright Act and the anti-circumvention prohibitions of 17 U.S.C. Section 1201. The original project was taken down on or about September 13, 2018,” the notice reads.
“The Forks of the ‘Fuckr’ repository are still active and equally violate the law, GitHub’s Terms, Grindr’s Terms, and endanger the safety of Grindr users by facilitating unauthorized access to the user’s location and exposing the user to real threats of anti-LGBT violence. Therefore, Grindr requests that these Forks be taken down for the same reasons as the original project.”
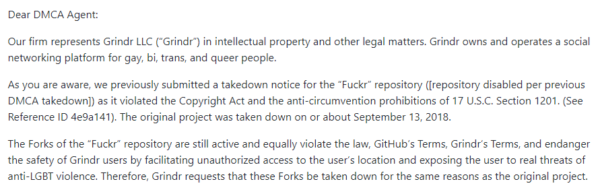
The DMCA takedown notice targets around 90 ‘forks’ or clones of the original Fuckr desktop application, showing that the process of removing the threat is still far from over.
Grindr says it has attempted to contact “the infringer” (presumably the people behind the original Fuckr) using the only address it was able to find, but its letters were returned as undeliverable. With that, the company seeks Github’s help to mitigate the ongoing problem.
“[W]e are certain GitHub will appreciate the gravity of the above-described violations and will not knowingly allow its services to perpetuate such illegal and threatening activity without swift action to protect the integrity of GitHub and members of the public who use its platform,” Grindr adds.
“Grindr respectfully requests GitHub immediately take down the Forks for the ‘Fuckr’ repository and appreciates a receipt of confirmation once the take down has been put into effect.”
Checks carried out by TF indicate that Github acted swiftly to disable the allegedly infringing repositories yesterday.
With so many clones of Fuckr still available online, it remains unclear why Grindr can’t make changes to its system to prevent Fuckr from gaining access to its data. Until it does, it seems likely that Fuckr will still remain a serious security threat to the company’s users.





