 As quite possibly the most people media player on earth, Kodi is installed on millions of machines – around 38 million according to the MPAA. The software has a seriously impressive range of features but one, if not configured properly, raises security issues for Kodi users.
As quite possibly the most people media player on earth, Kodi is installed on millions of machines – around 38 million according to the MPAA. The software has a seriously impressive range of features but one, if not configured properly, raises security issues for Kodi users.
For many years, Kodi has had a remote control feature, whereby the software can be remotely managed via a web interface.
This means that you’re able to control your Kodi setup installed on a computer or set-top box using a convenient browser-based interface on another device, from the same room or indeed anywhere in the world. Earlier versions of the web interface look like the one in the image below.
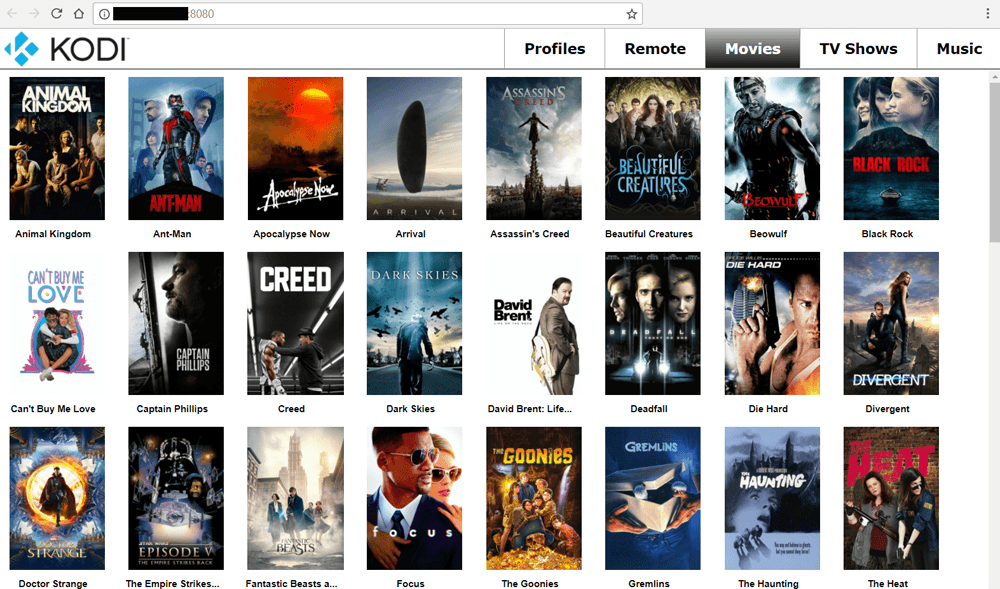
But while this is a great feature, people don’t always password-protect the web-interface, meaning that outsiders can access their Kodi setups, if they have that person’s IP address and a web-browser. In fact, the image shown above is from a UK Kodi user’s setup that was found in seconds using a specialist search engine.
While the old web-interface for Kodi was basically a remote control, things got more interesting in late 2016 when the much more functional Chorus2 interface was included in Kodi by default. It’s shown in the image below.
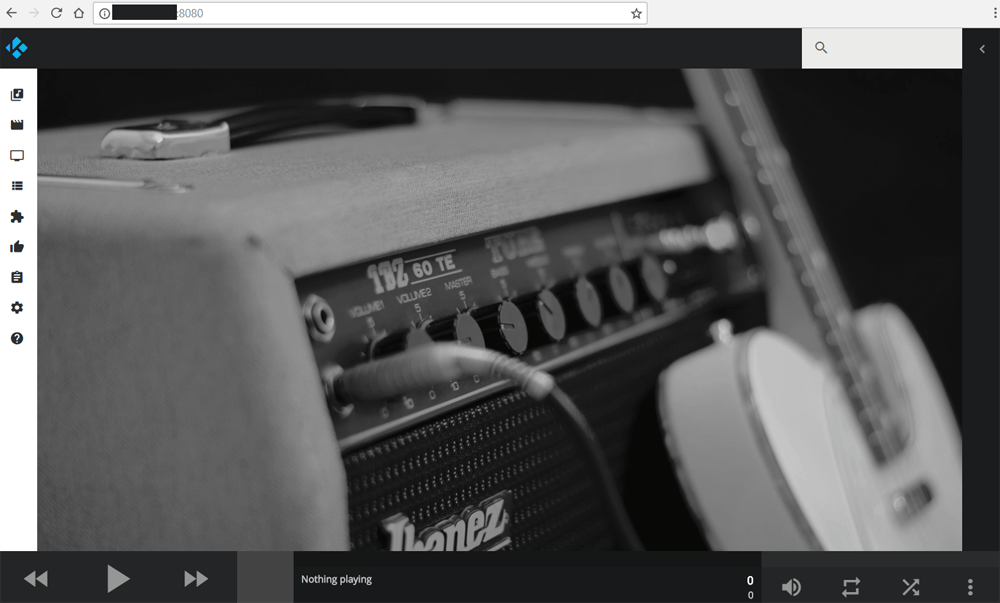
Again, the screenshot above was taken from the setup of a Kodi user whose setup was directly open to the Internet. In every way the web-interface of Kodi acts as a web page, allowing anyone with the user’s IP address (with :8080 appended to the end) to access the user’s setup. It’s no different than accessing Google with an IP address (216.58.216.142), instead of Google.com.
However, Chorus 2 is much more comprehensive that its predecessors which means that it’s possible for outsiders to browse potentially sensitive items, including their addons if a password hasn’t been enabled in the appropriate section in Kodi.

While browsing someone’s addons isn’t the most engaging thing in the world, things get decidedly spicier when one learns that the Chorus 2 interface allows both authorized and unauthorized users to go much further.
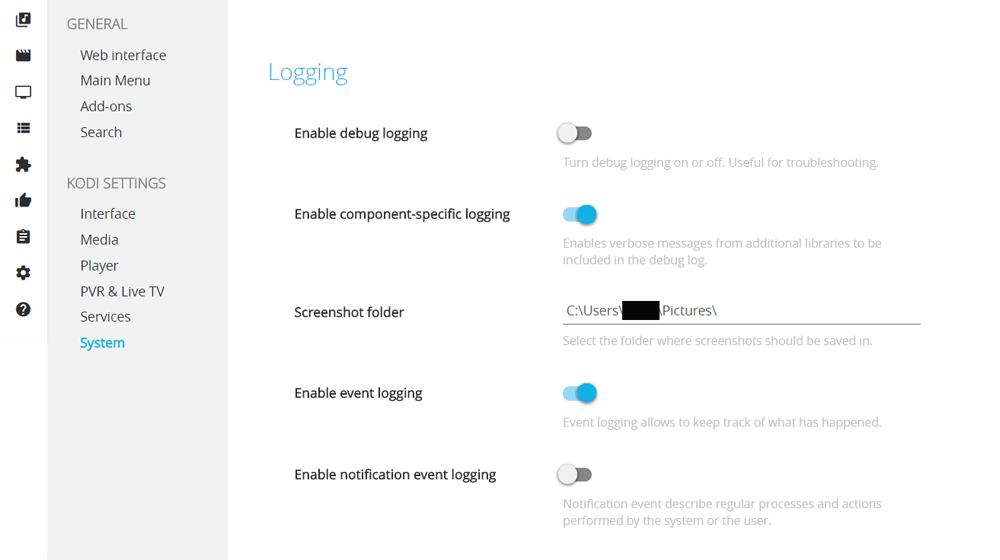
For example, it’s possible to change Kodi’s system settings from the interface, including mischievous things such as disabling keyboards and mice. As seen (or not seen) in the redacted section in the image below, it can also give away system usernames, for example.
But aside from screwing with people’s settings (which is both pointless and malicious), the Chorus 2 interface has a trick up its sleeve. If people’s Kodi setups contain video or music files (which is what Kodi was originally designed for), in many cases it’s possible to play these over the web interface.
In basic terms, someone with your IP address can view the contents of your video library on the other side of the world, with just a couple of clicks.
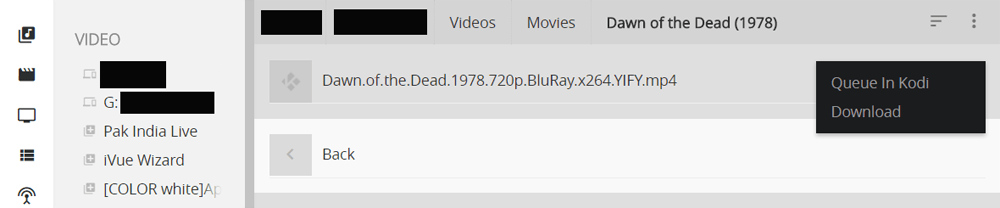
The image below shows that a Kodi setup has been granted access to some kind of storage (network or local disk, for example) and it can be browsed, revealing movies. (To protect the user, redactions have been made to remove home video titles, network, and drive names)
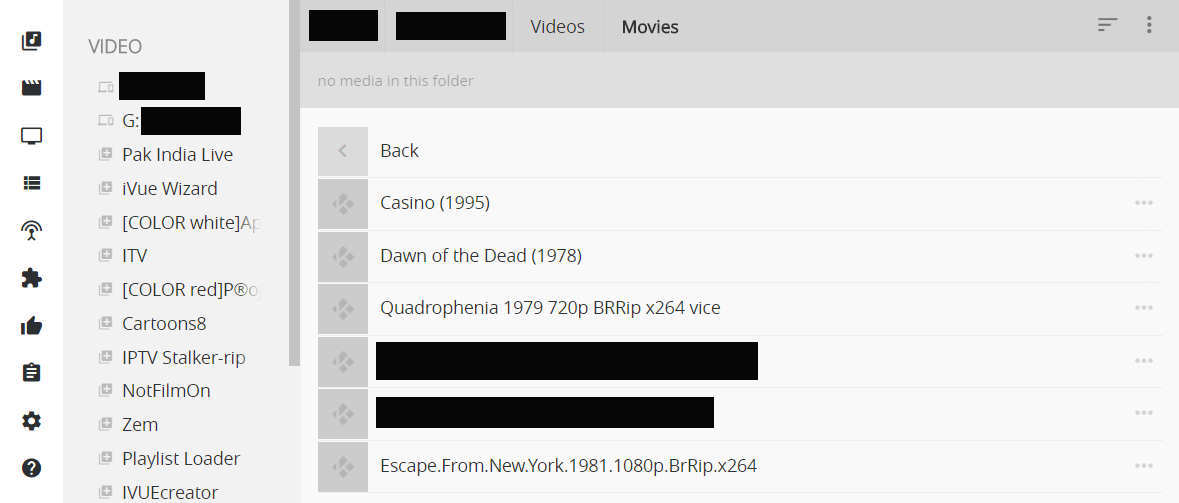
The big question is, however, whether someone accessing a Kodi setup remotely can view these videos via a web browser. Answer: Absolutely.
Clicking through on each piece of media reveals a button to the right of its title. Clicking that reveals two options – ‘Queue in Kodi’ (to play on the installation itself) or ‘Download’, which plays/stores the content via a remote browser located anywhere in the world. Chrome works like a charm.
While this is ‘fun’ and potentially useful for outsiders looking for content, it’s not great if it’s your system that’s open to the world. The good news is that something can be done about it.
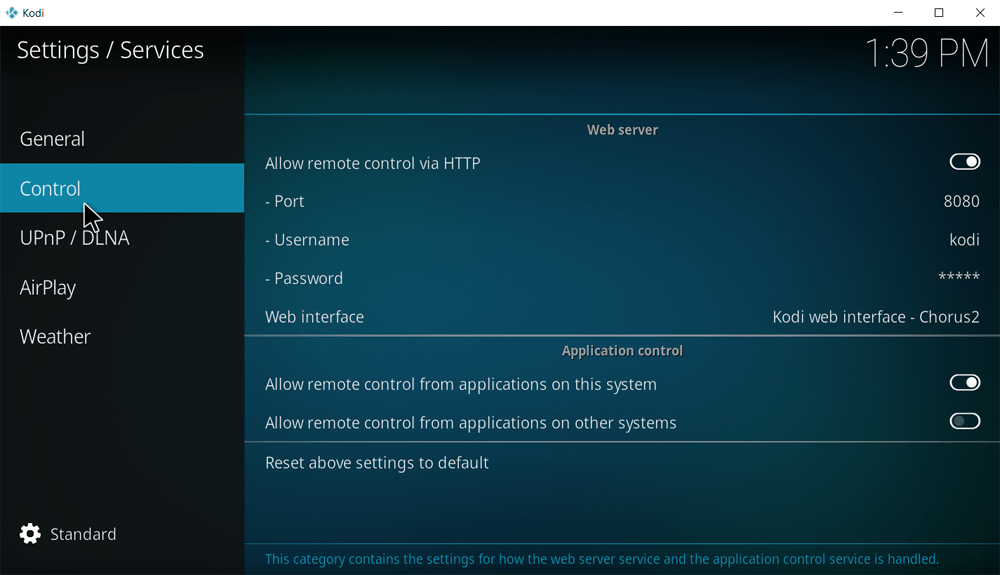
In their description for Chorus 2, the Kodi team explain all of its benefits of the interface but it appears many people don’t take their advice to introduce a new password. The default password and username are both ‘kodi’ which is terrible for security if people leave things the way they are.
If you run Kodi, now is probably the time to fix the settings, disable the web interface if you don’t use it, or enable stronger password protection if you do.
Just recently, Kodi addon repository TVAddons issued a warning to people using jailbroken Apple TV 2 devices. That too was a default password issue and one that can be solved relatively easily.
“People need to realize that their Kodi boxes are actually mini computers and need to be treated as such,” a TVAddons spokesperson told TF.
“When you install a build, or follow a guide from an unreputable source, you’re opening yourself up to potential risk. Since Kodi boxes aren’t normally used to handle sensitive data, people seem to disregard the potential risks that are posed to their network.”





